Render unto Caesar the things that are Caesar's...
Or more exactly to Vulcainreo (Arnaud Courty), who develops an opensource IoT learning board. You can acquire it for less than 40€, which I did myself at Grehack, on the good advice of my awesome colleagues ghozt and shoxx. DVID aims to familiarize the security community with hardware hacking. A series of challenges going through UART and bluetooth are currently released, and more will follow, with Wi-Fi, Lora, Zigbee, and maybe more, who knows! However, we will begin with the Bluetooth series (BLE to be precise). Let's get our hands dirty (kind of)!
Advertising
Goal
- A confidential message is stored on the firmware but protected by a password
- The goal is to provide a screenshot of the confidential message
Tips
- Hey ! Advertise me to know my name
Result
- The password is an animal name.
If you have ever used Bluetooth in your life, you are aware that Bluetooth enabled device advertise their name to allow other devices to pair with them. Let's use the bluetoothctl tool to discover available devices. First, make sure that the bluetooth service is up.
systemctl restart bluetooth.service
Then, launch bluetoothctl, and power on the adapter.
bluetoothctl power on
Finally gotta scanem'all!

For the last step, we just have to submit the name of the device via UART, and we'll get our animal name!

Characteristics
Goal
- One time password bluetooth device
- Works with an android application, but you don't have it
- The goal is to provide a screenshot of the password
Tips
- Verbose mode = 1 on 0000ffe1
Result
- The password is an animal name
According to this site, GATT is an acronym for the Generic Attribute Profile, and it defines the way that two Bluetooth Low Energy devices transfer data back and forth using concepts called Services and Characteristics.
A nice tool to scan for bluetooth services and characteristics is btgatt-client.

However, nothing special stands out at first sight on 0000ffe1 address. Using bleah, it is clearer that something wierd is going on there.
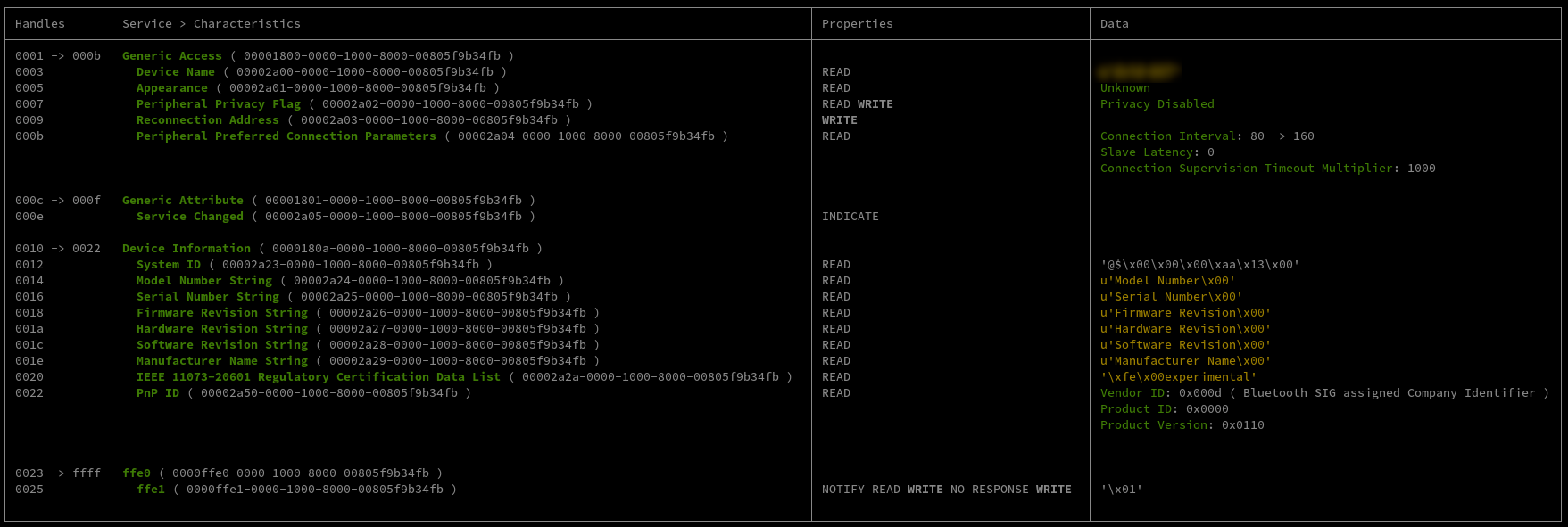
The address indeed allows extended permissions. Now, how to get the content of this characteristic? Let's go back to btgatt-client, and turn on the "verbose" option.
btgatt-client -d _dest_macaddress -e -v
From there, you will probably notice that a shitload of information is printed on your screen, and at some point, these lines:

The password is displayed periodically, just like an OTP may do. And another animal!

Characteristics 2
Goal
- A confidential message is stored on the firmware but protected by a password
- The goal is to provide a screenshot of the confidential message
Tips
- Come on to say hello on 0000ffe1
Result
- The password is an animal name
Without surprise, we should attempt to write the charateristic mapped on the 0X0000ffe1 address. We already have all the info we need, using our last scan with bleah. Let's write "hello" on handle 0x0025.
bleah -b 00:13:aa:00:24:40 -n 0x0025 -d "hello"

Yay! Our final animal is displayed on the board's screen.

Final thoughts
Vulcainreo did a really good job by putting this board together, allowing hardware noobs like me to enjoy a step by step journey in this new world. Now I am just waiting for new challenges to be released! For more advanced techniques on hardware hacking, here is a nice writeup on cracking the badge challenge of Grehack by ghozt.
Need offensive security services, or application security support? CryptID has got you covered!
