Introduction
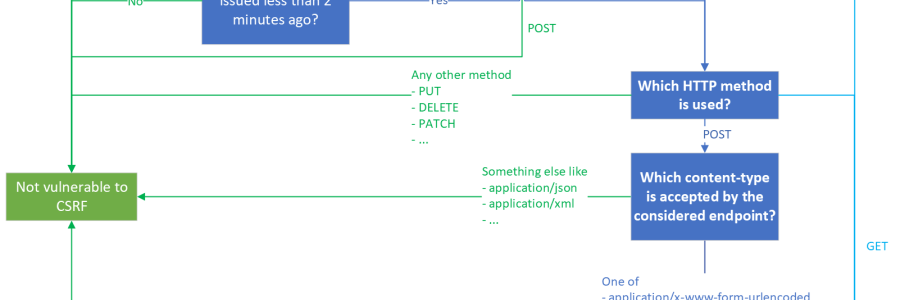
In the last blog post, we detailed the various conditions necessary to perform a successful CSRF attack, considering today's browser security. I mentioned that it was mostly written out of frustration, as I received numerous erroneous pentest reports regarding CSRF... Well, it see...
Introduction
A couple of years ago, CORS misconfigurations were the hot stuff for Bug Bounty hunters. Now, the vulnerability has made its way to penetration tests reports, along with CSRF and other self-XSS poor man's security issues. The thing is, the state of the art of security for browse...
TL;DR it was more tedious than expected
As a proud owner of an ACR122U NFC reader, I periodically try to read the content of my own cards, out of interest. This device can only work on the 13.56 MHz and is fairly limited compared to a Proxmark3, but is much cheaper, which is also an important fact...
When pentests are not enough
I am not a devoted adept of sytematic code reviews, and find that most of the time, penetration tests cover 80% of the vulnerabilities in a much shorter timeframe. Let's face it : usually, the return on investment is just much better. However, for complex pieces of sof...
Apologies
Dear readers, I apologize sincerely. This blog was supposed to be about security, however my first post will be related to system administration. That said, let's get our hands dirty!